If you’re seeking a job in Governance, Risk, and Compliance (GRC) and aiming to grasp the fundamentals of auditing and risk assessments, but lack a company to audit, you’re in luck. In this post, I’ll demonstrate how you can utilize ChatGPT as a surrogate Company for your practice. We’ll be employing the NIST 800-53 framework for the audit process. For risk assessment, a valuable resource is the NIST 800-30, which offers insights into the likelihood and impact on an organization. While not the only approach, these resources serve as excellent starting points and references for assessing risk effectively.
Overview
In this lab session, I’ll instruct ChatGPT to simulate a company while conducting an interview to evaluate its security posture against the NIST 800-53 Framework. Using Excel, I’ll document my findings and risk assessment of this fictional entity. While the NIST 800-53 comprises 20 control families and over 1000 security controls, my focus will narrow down to the Risk Assessment (RA) family, specifically RA-1 to RA-5. The goal is to provide a glimpse into the auditing process, emphasizing the importance of robust risk management practices aligned with industry standards and regulatory requirements. The audit scope aims to safeguard the organization’s assets, operations, and reputation by mitigating security risks effectively.
What is the NIST 800-53?
The NIST (National Institute of Standards and Technology) Special Publication 800-53 is a framework that provides a comprehensive set of security controls and guidelines for federal information systems and organizations handling sensitive information. The NIST 800-53 serves as a foundational resource for organizations seeking to establish robust cybersecurity practices and protect their information systems from various threats and vulnerabilities.
What you need for this lab
- NIST 800-53 (PDF)
- NIST 800-53 (Spreadsheet)
- NIST 80-30 (Risk Assessment Reference)
- ChatGPT
Note: These links are straight from the NIST website.
Let’s Get Started
The first thing we are going to do is create our spreadsheets.
Get your spreadsheet from the NIST 800-53 and get ready to record your findings. For this lab, we are using the base controls so don’t worry about the control enhancements. You can use either Google Sheets or Microsoft Excel. For this Lab, I am going to use Excel. Once you download the spreadsheet it should have all the controls of the NIST 800-53 and scroll down to the RA-1 security control.
It should look like this:
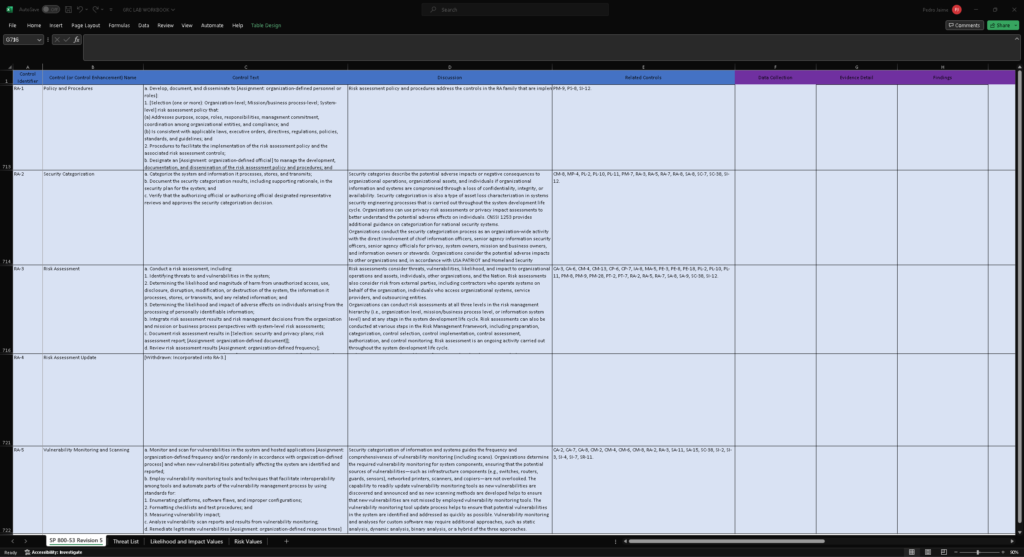
In a real environment, simply submitting this spreadsheet to stakeholders wouldn’t suffice. Consider this spreadsheet as a backup tool in case you encounter any resistance and require evidence to support your findings. Its primary purpose is to facilitate information gathering as you prepare the final report.
In my spreadsheet, I added:
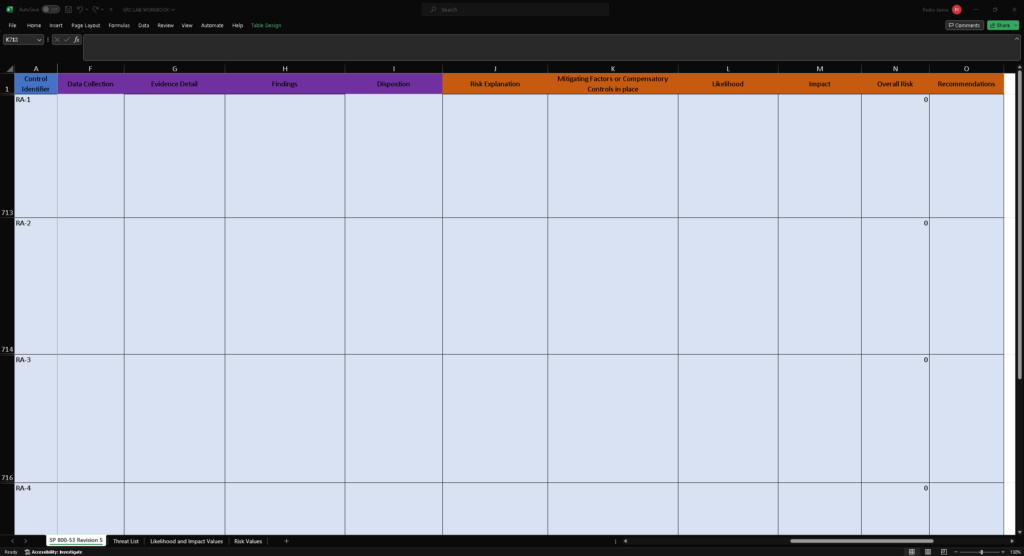
As you can see I added more columns to the spreadsheets to record my audit findings and conduct my risk assessment. The purple section is for my Auditing and my orange section is for my Risk Assessment.
We are going to give it this prompt:
I want you to act as the head of the information security department at a make-believe company and I will be interviewing you for a compliance audit using the NIST 800-53 framework focusing on Risk Assessment. Give yourself a name and also the company a name. I will ask you questions about security controls to see if you have them in place or not and just give me an answer but make it realistic by not having some controls in place in some of the questions I ask you and be sure to tell me where you are lacking if you don’t have some security controls in place. Is that possible?
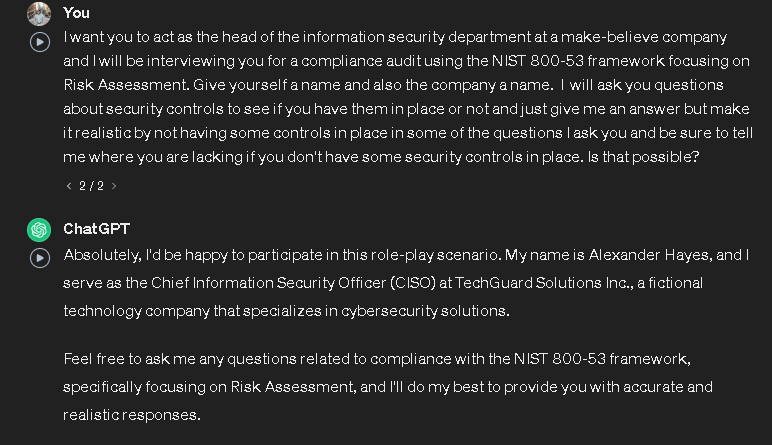
After giving ChatGPT the prompt, it gave me this response. So on my spreadsheet, under Data Collection, I put that this will be an interview, and under Personnel, I added Alexander Hayes. This process allows me to track the origin and methodology of each piece of evidence obtained, ensuring transparency and accountability for every control assessed.
Now let’s get started with the Auditing part of this Lab. I will now start asking ChatGPT questions. The questions I will be asking are from the controls RA-1-RA-5. Although you can copy and paste the control from the NIST 800-53 document and insert it into ChatGPT, it’s better to create a question in your own words in a separate document, covering the controls. This is because if you are auditing a real person, it’s not ideal to just read from the document. You will just confuse whoever you are auditing. It’s your job to make it more understandable for the person you are interviewing for a better experience and detailed response. You should do this with this framework and also any other ones out there.
For example, These are the questions I will be asking:

Now that we have the questions we are asking, let’s ask ChatGPT some questions! First I am going to ask “What are the policies and procedures around Risk Assessment?”
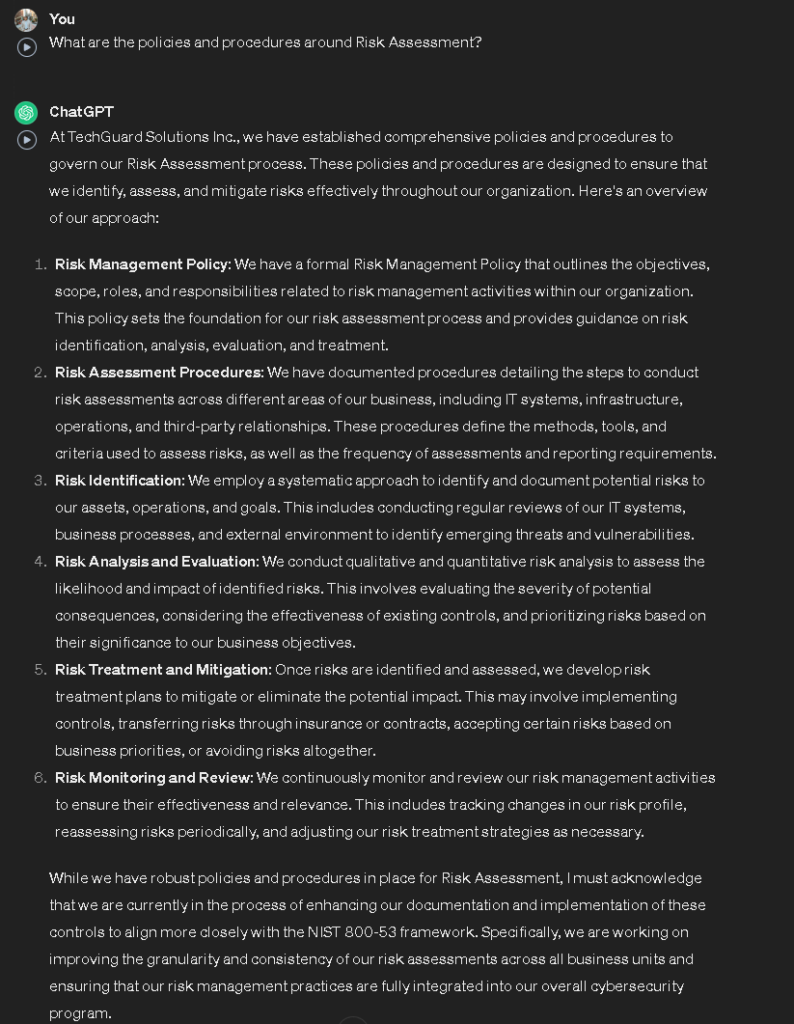
It seems TechGuard Solutions Inc. has policies and procedures available regarding Risk Assessments. In this case, we do not have to do a risk assessment because they have this security control in place. Let’s update our spreadsheets:

So now, we move on to the next question.
The second question will be asking is for RA-2, “Can you describe the process of categorizing systems and the information they handle? Are you documenting these categorizations and the reasoning behind them? If so, Who is authorizing and approving these decisions?”
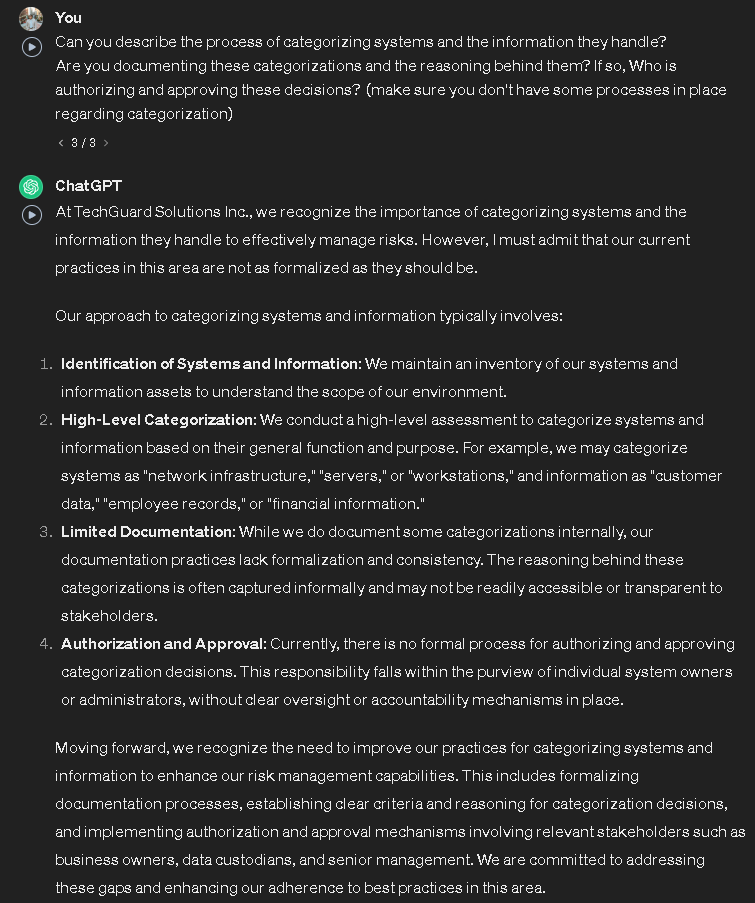
If you noticed I asked ChatGPT to make sure it has some gaps when it comes to these controls to practice doing a risk assessment because it tends to answer all the questions correctly. Based on this response, it looks like they have a process on how they categorize their systems but it’s very adequate also documentation is not done properly nor it’s approved so they basically just have an unofficial document. In that case, this control is partially in place. To do our risk assessment I am following the likelihood and impact values from NIST 80-30. Here are the values:
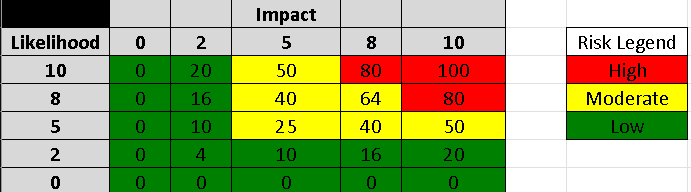
Go through the document to learn more about these values and their description. To assess the overall risk you multiply the likelihood and impact. Based on this heat map you label the risk as Low, Medium, and High.
Let’s update the spreadsheet:
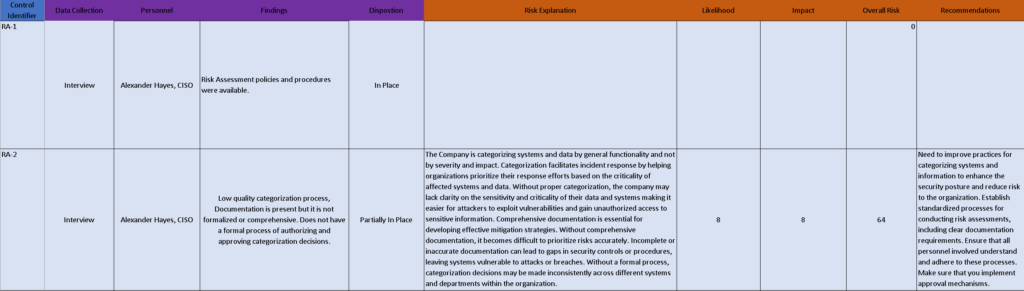
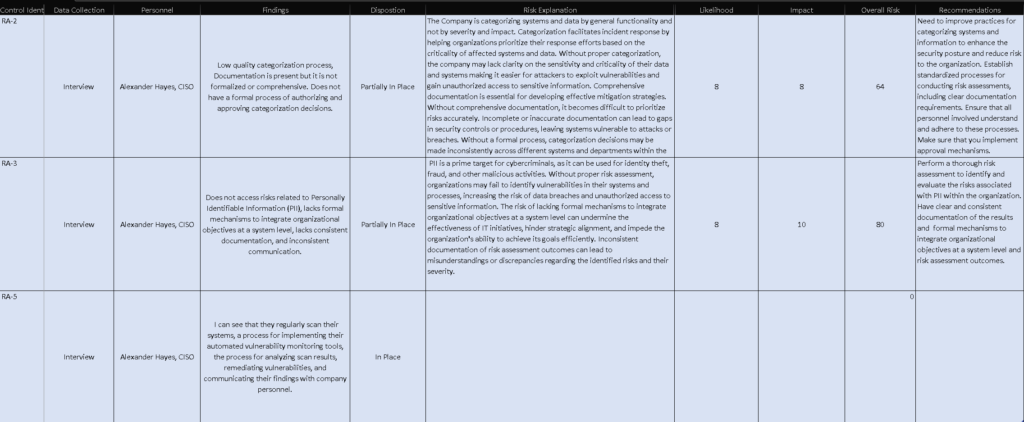
Here is the updated spreadsheet (zoom in if you have to). This company needs to improve practices for categorizing systems and information to enhance the security posture and reduce risk to the organization. They also need to establish standardized processes for conducting risk assessments, including clear documentation requirements. Ensure that all personnel involved understand and adhere to these processes and make sure that you implement approval mechanisms.
Regarding the risk assessment, I said that the likelihood is an 8 meaning an Adversary is highly likely to initiate the threat event, and the impact is an 8 as well meaning it is expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, individuals, other organizations, or the Nation.
Let’s move on to the next question.
For RA-3 I asked, “Can you describe the process of identifying threats and vulnerabilities systems, assessing the likelihood and impact of a security breach, and evaluating risks related to Personally Identifiable Information? How do you ensure the risk assessment results are integrated with organizational Objectives and mission/business processes at the system level? Could you explain how you document the outcomes of the risk assessment, how often these results are reviewed, who receives them, and how often the risk assessment is updated?”

After reading, I found that TechGuard Solutions Inc. does not address risks related to Personally Identifiable Information (PII), lacks formal mechanisms to integrate organizational objectives at a system level, lacks consistent documentation, and inconsistent communication.
Let’s update the spreadsheet

For this risk assessment, I said that, I said that the likelihood is an 8 meaning an Adversary is highly likely to initiate the threat event, and the impact is an 8 as well meaning it is expected to have multiple severe or catastrophic adverse effects on organizational operations, organizational assets, individuals, other organizations, or the Nation. PII is extremely sensitive data and an adversary getting a hold of that data can lead to can lead to identity theft, fraud, financial loss, reputational damage, operational disruption, and more.
For RA-4, we can disregard this one since it is Incorporated into RA-3.
Lastly, we are going to do RA-5. The question I am going to ask is “How do you regularly monitor and scan for system and application vulnerabilities and respond to new vulnerabilities? How do you implement vulnerability monitoring tools and techniques that are practical and automate the vulnerability management processes? Describe the process of analyzing the results of the scan and how you remediate vulnerabilities. How are you communicating the findings with designated personnel or roles to enhance system security?”
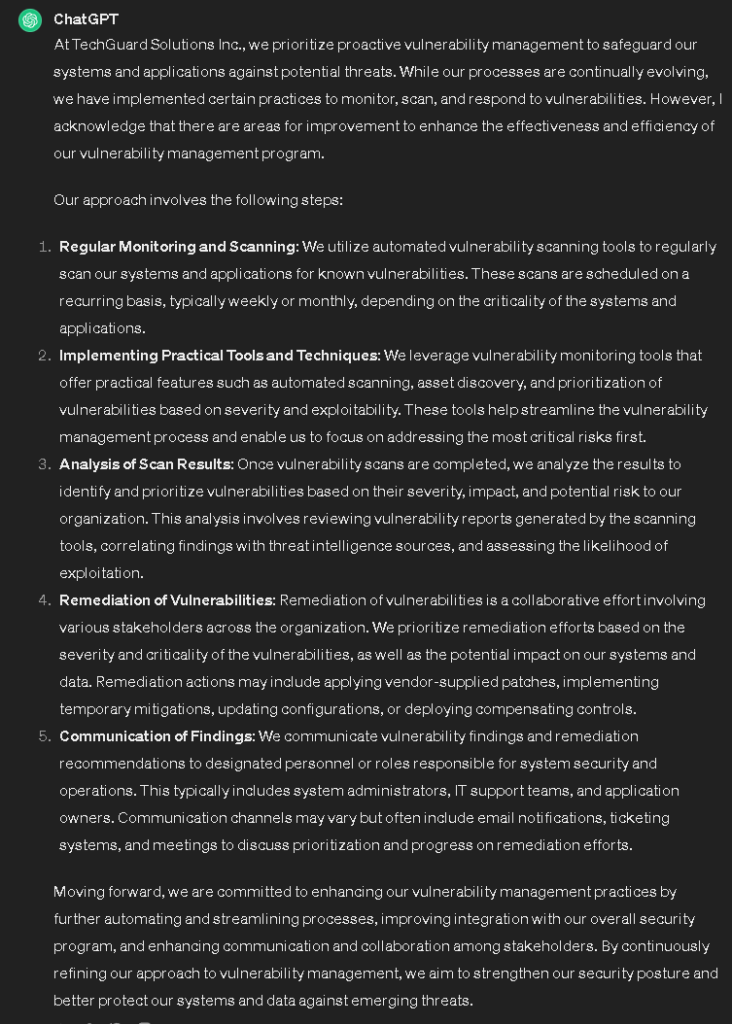
Based on the response, I can see that they regularly scan their systems, a process for implementing their automated vulnerability monitoring tools, the process for analyzing scan results, remediating vulnerabilities, and communicating their findings with company personnel. This shows me that comply with security control RA-5. Since they have this security control we do not have to do a risk assessment.
Final update of the spreadsheet:
Conclusion
In conclusion, for this Lab, we only went through RA-1 – RA-5 in the Risk Assessment Family. For RA-1 and RA-5 the security controls were in place, however, for RA-2 and RA-3 the security controls were not in place so we did a risk assessment on an Excel spreadsheet covering why this is a threat, the likelihood of security event, the impact of a security breach can have on the organization, Overall risk determining the severity of the risk, and even recommendations to enhance security posture. In a real-world environment, after doing your audits and risk assessment, you would make a report on your findings, communicate the findings with stakeholders, and try to explain to them in a nontechnical way the risk you found, why it is a risk, what detrimental impact it can have on the organization, and mitigation strategies.
I trust you found value in this lab and gained insights into conducting security audits and risk assessments. I encourage further exploration of resources like the NIST 800-53 framework, as well as other frameworks such as NIST CSF, CIS, PCI-DSS, SOX, SOC2 ISO 27001, HIPAA, etc. By exploring these frameworks, you’ll further refine your skills in this critical area of cybersecurity. Remember, practice is essential for mastering the art of audit and risk assessment. Engaging in additional labs and real-world scenarios will undoubtedly strengthen your proficiency.